Disclaimer: The views expressed in my posts on this site are mine & mine alone & don’t necessarily reflect the views of Microsoft. All posts are provided “AS IS” with no warranties & confers no rights. If I post any code, scripts or demos, they are provided for the purpose of illustration & are not intended to be used in a production environment. They are provided ‘as is’ without warranty of any kind, expressed or implied, including but not limited to the implied warranties of merchantability and/or fitness for a particular purpose. I grant you a nonexclusive, royalty-free right to use & modify my sample code & to reproduce & distribute the object code form of the sample code, provided that you agree: (i) to not use my name, my companies name, logo, or trademarks to market your software product in which the sample code is embedded; (ii) to include a valid copyright notice on your software product in which the sample code is embedded; and (iii) to indemnify, hold harmless, and defend me, Microsoft & our suppliers from & against any claims or lawsuits, including attorneys’ fees, that arise or result from the use or distribution of the sample code.
Updated: May 3rd, 2020
Published: May 1st, 2020
Applies to:
Windows Server, version 1909 (Core edition)
Windows Server, version 1903 (Core edition)
Windows Server 2019 Core edition (1809)
Windows Server, version 1803 (Core edition)
I was curious how Windows Server 1909 Core edition would fair against some of the live antimalware payloads that are out there today.
Warning: All precautions of handling a live malware were taken before hand.
I first had to disable “Windows Defender Smartscreen for Microsoft Edge” otherwise, it was catching and deleting the files.
Then I had to turn off “Real-time protection” in Windows Defender Antivirus (WDAV) in order to be able to actually download and run the malware payloads.
Here are the results of my tests…
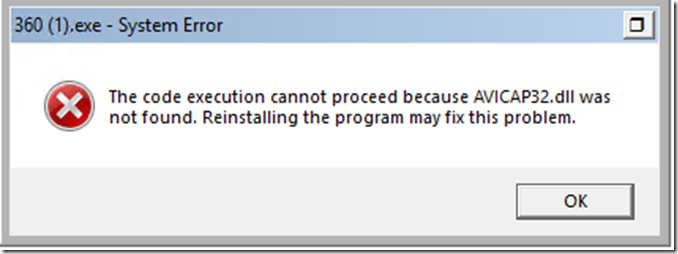
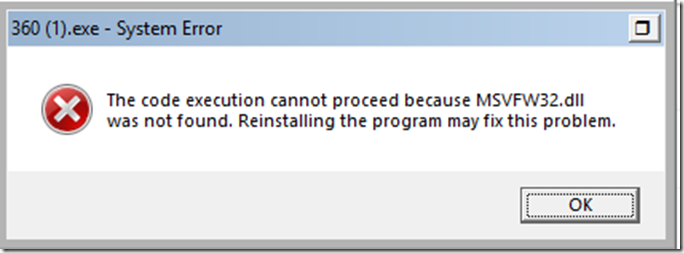
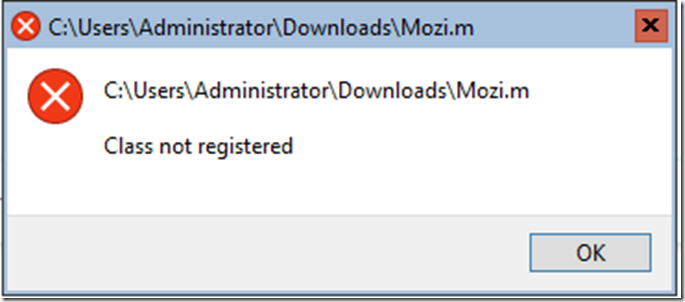
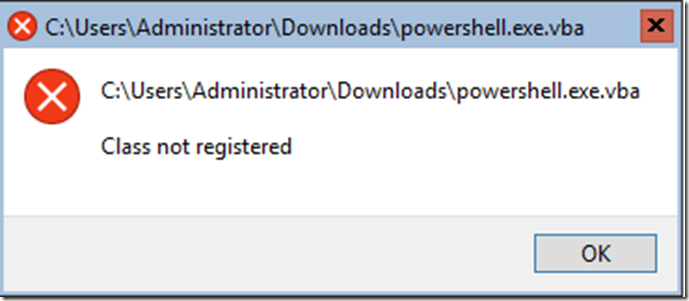
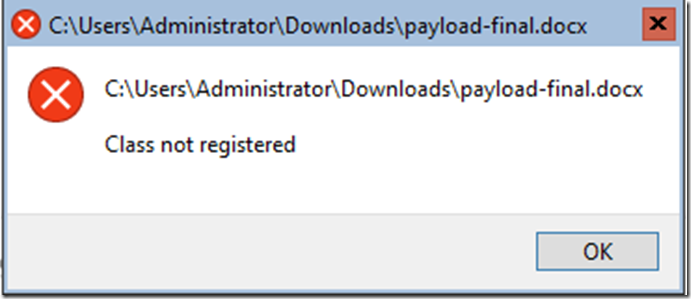
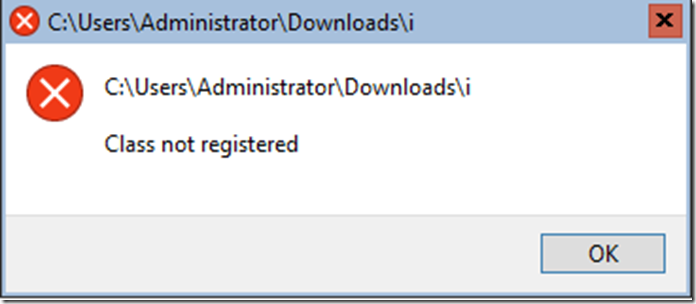
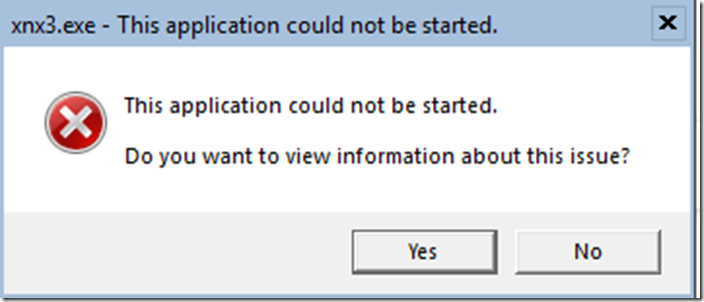
A lot of the malware had dependencies thus failed to launch altogether.
Even these that lacked to launch, the Enterprise class leading ‘Windows Defender Antivirus’ (WDAV, Endpoint Protection Platform (EPP)) caught them and quarantined it.
And for additional visibility we had the Enterprise class leading ‘Microsoft Defender Advanced Threat Protection’ (MDATP, Endpoint Detection and Response (EDR)) running and keeping an eye.
What is the Server Core installation option in Windows Server?
https://docs.microsoft.com/en-us/windows-server/administration/server-core/what-is-server-core
Roles, Role Services, and Features included in Windows Server – Server Core
https://docs.microsoft.com/en-us/windows-server/administration/server-core/server-core-roles-and-services
Administer a Server Core server
https://docs.microsoft.com/en-us/windows-server/administration/server-core/server-core-administer
Manage a Server Core server
https://docs.microsoft.com/en-us/windows-server/administration/server-core/server-core-manage
| The good | The challenge | |
| A smaller footprint, thus a smaller ‘attack surface area’ than Windows Server with ‘Desktop Experience’ (a GUI) | You should know Powershell to manage it
or Can use Windows Admin Center |
|
| On Windows Server 2016 core or newer, it requires just 1 security update per month.
On Windows Server 2012 R2 core or older, it requires fewer software updates and reboots |
Application compatibility | |
| Less overhead since it has fewer services and the ‘shell’ is a command prompt (cmd.exe) instead of Explorer.exe running without the GUI. Meaning less MB’s but nowadays with servers with GB’s and TB’s… folks might not be counting the MB’s. |
No Accessibility support | |
| No audio support | ||
| Starting with Windows Server 2016 you cannot switch back and forth between a GUI and Core.
Switching between Windows Server 2016 Server Core and Desktop Experience |
Thanks,
Yong
Twitter: @YongRheeMSFT
https://twitter.com/yongrheemsft
P.S. Related content regarding these series:
Evaluation (PoC) Guide for Microsoft Defender Antivirus (MDAV) and Microsoft Defender–Exploit Guard [Attack Surface Reduction Rules, Controlled Folder Access and Network Protection]
https://yongrhee.wordpress.com/2020/03/03/evaluation-poc-guide-for-microsoft-defender-antivirus-mdav-and-microsoft-defender-exploit-guard-attack-surface-reduction-rules-controlled-folder-access-and-network-protection/
Do macOS need an antimalware (antivirus) and EDR software?
https://yongrhee.wordpress.com/2020/03/08/do-macos-need-an-antimalware-antivirus-and-edr-software/
SCCM-Endpoint Protection: Microsoft Defender Advanced Threat Protection (EDR) for Windows Server 2019 (Part 14)
https://yongrhee.wordpress.com/2020/03/29/sccm-endpoint-protection-microsoft-defender-advanced-threat-protection-edr-for-windows-server-2019-part-14/
SCCM-Endpoint Protection: Microsoft Defender Advanced Threat Protection (EDR) for Windows 7 SP1, Windows 8.1, Windows Server 2008 R2 SP1, Windows Server 2012 R2, and Windows Server 2016 (Part 15)
https://yongrhee.wordpress.com/2020/04/16/sccm-endpoint-protection-microsoft-defender-advanced-threat-protection-edr-for-windows-7-sp1-windows-8-1-windows-server-2008-r2-sp1-windows-server-2012-r2-and-windows-server-2016-part-15/